Graylog
Graylog’s vision is a secure digital world where organizations of all sizes can effectively guard against cyber threats. They’re committed to turning this vision into reality by providing Threat Detection & Response that sets the standard for excellence. Their cloud-native architecture delivers SIEM, API Security, and Enterprise Log Management solutions that are not just efficient and effective – whether hosted by us, on-premises, or in your cloud – but also deliver a fantastic Analyst Experience at the lowest total cost of ownership. Graylog aims to equip security analysts with the best tools for the job, empowering every organization to stand resilient in the ever-evolving cybersecurity landscape.
Graylog Security
Empowering Your Cybersecurity with Advanced SIEN Technology
Given the increasing cyber threats, organizations must prioritize efficient threat detection and incident response (TDIR). A robust SIEM solution is indispensable for CISOs dealing with both advanced cyber-attacks and budget constraints. Without such a system, companies face significant risks, including data breaches, financial losses, and reputational harm. Effective SIEM systems offer comprehensive visibility and advanced analytics, essential for protecting against cybercriminals and maintaining business continuity.
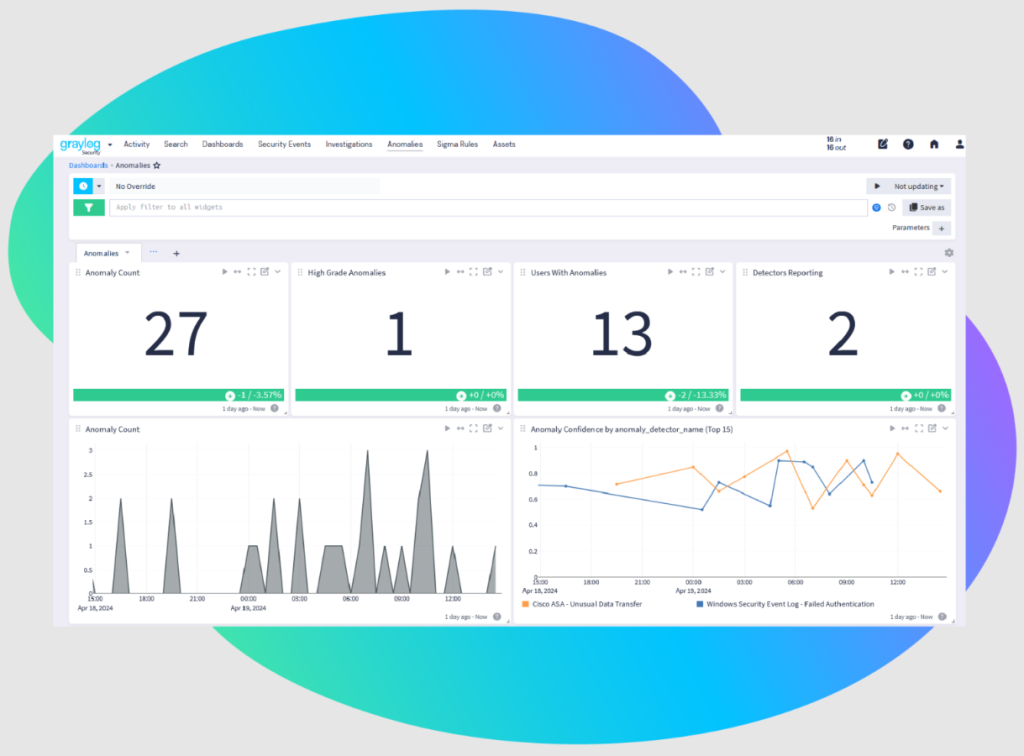
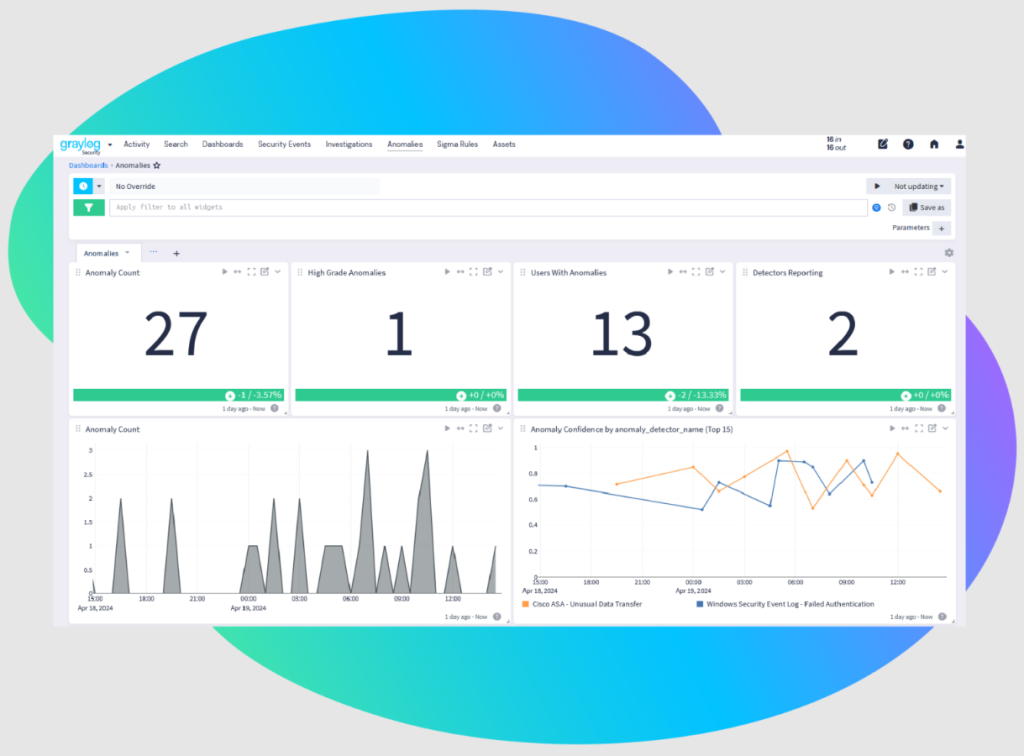
Graylog Enterprise Log Management
The Art of Centralized Log Management, Mastered.
In today’s rapidly changing digital landscape, data reigns supreme, and logs are its chroniclers. Every byte of log data, from modest servers to expansive security systems, weaves a narrative. However, without the proper tools, this narrative remains untold, akin to a library with a million unsorted books. This is where Graylog Enterprise steps in, redefining centralized log management (CLM). It’s not merely about gathering data; it’s about extracting meaningful value from it.
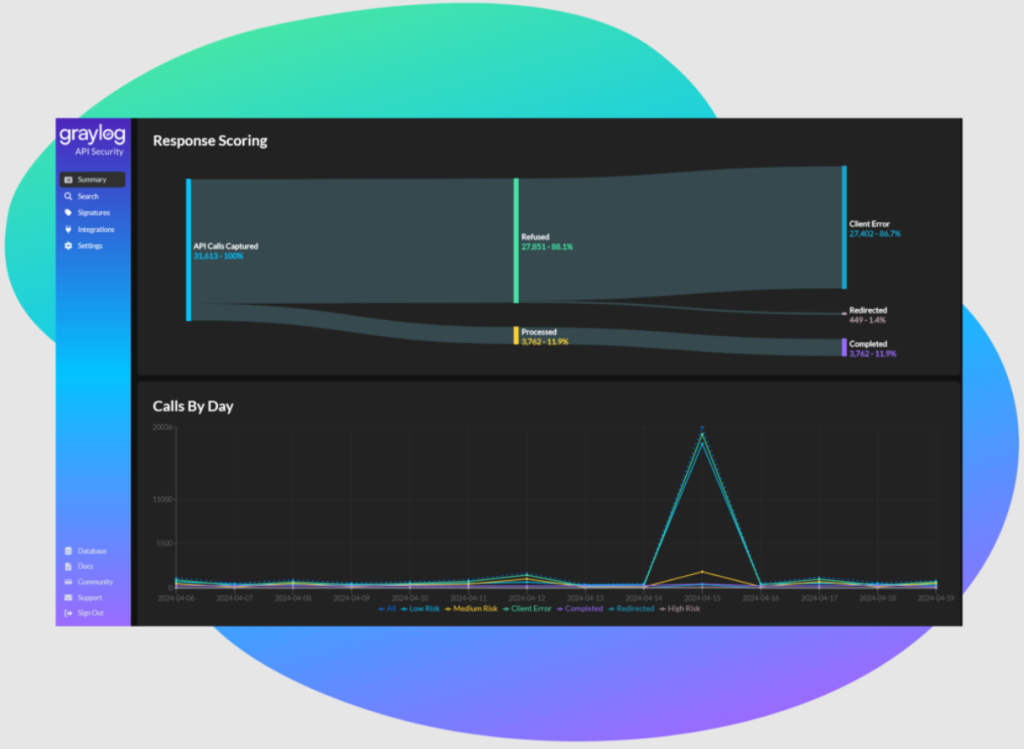
Graylog API Security
The Ultimate Solution for End-to-End API Threat Monitoring, Detection, and Response
APIs are crucial for internet traffic and business continuity, acting as gateways to software applications and exposing parts of a business’s internal functions to the external world. In today’s interconnected digital ecosystem, cyberattacks are becoming increasingly sophisticated, making APIs more vulnerable if not properly secured.